The mainstream electronic locks on the market are based on password design. The biggest drawback of password locks is that passwords are easily stolen, guessed, and forgotten by others. With the development of biotechnology, more and more living technologies are applied to recognition systems such as fingerprints, palm prints, faces, and irises. Compared with other living recognition technologies, fingerprint recognition systems are more and more applicable to various occasions because of their achievability, relatively low cost, and high security. The paper presents a new type of fingerprint lock architecture, and discusses in detail the various components of the system and the implementation process of the fingerprint recognition algorithm. The article proposes a unique approach to reducing system power consumption and increasing confidentiality.
With the rapid development of science and technology and the emergence of large-scale integrated chips, the existing door lock system is undergoing an upgrade. The first generation of electronic door locks uses a password identification method, which solves the flexibility of mechanical door lock replacement, that is, the setting and modification of the key is in the hands of the user; but because the key is not strongly correlated with the user, the loose coupling Authorization is difficult to manage, and there are great hidden dangers in terms of security. The second generation of electronic door locks uses the most advanced biometric technology to provide a new way to identify, safer, more reliable and easy to use.
Biometrics technology mainly uses iris, face, fingerprint, palm print, and voice to identify one of several human biological characteristics. Iris and face need to use image imaging system, the device is too complicated, only for high-end systems, it is difficult to popularize the application; the voice system is the simplest, but because it is easy to be imitated, the security is relatively low; fingerprint and palm print only use scanning imaging It is relatively simple and easy to promote, especially the fingerprint recognition technology. With the progressive scan system, the recognition sensor can be made very small, with high feasibility and practicability.
The fingerprint lock system can be mainly used for identity confirmation and related control of safes, laboratories, corridors; with the rise of the smart home concept, more and more applications are applied to high-end residences.
1 fingerprint lock architecture
The hardware structure of the fingerprint lock system mainly includes: a fingerprint recognition head, a main processing microcontroller, a power management, an electric lock mechanism, and an infrared sensing and alarm circuit required for the door lock function, wherein the core part is a fingerprint recognition head and a main part. Handle the microcontroller. The hardware structure block diagram of the fingerprint lock system is shown in Figure 1.
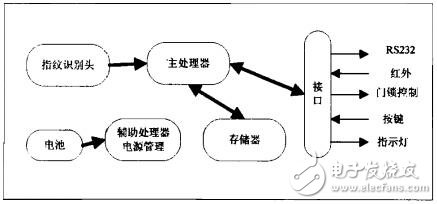
Figure 1 Fingerprint door lock hardware structure block diagram
The fingerprint lock acquires the original fingerprint data through the fingerprint recognition head, extracts the relevant fingerprint feature through the processing of the main processor, and then compares with the fingerprint template in the memory, and if the fingerprint features match, the corresponding indication is made by the indicator light, and at the same time The door lock opening signal is output, and the door lock is opened; when the door lock is opened, the fingerprint template storage can also be performed by corresponding button operations.
The auxiliary processor is used for power management of the system, that is, managing the power-on and off of the main processor. This design adopts a hierarchical and inclusive architecture design. The main processor is powerful, the processing function is relatively complex, and the power consumption is high. The auxiliary processor function is very simple. It is only responsible for power management, and completes the power-on and power-off processing of the system (except that it does not power off). The architecture has three advantages. First, the power consumption is extremely low. In the system standby mode, the main processor portion does not consume power at all, and the system can stand by for a long time. Second, with a hierarchical architecture, the two processor functions are completely decoupled, and the software can be freely evolved separately. Third, super-reliability, as the number of lines of code increases, the anomaly increases exponentially, so the reliability of the main processor program for a long time is greatly reduced. This architecture adopts the scheme of the auxiliary processor. The processor handles the power-off state most of the time. Every time it works, it has undergone a power-on process. Therefore, in principle, the main processor can achieve the reliability of never crashing; and the auxiliary processor works extremely simple: detecting touch, Then power up the main processor, wait for the main processor to idle, and then power down the main processor. The program code line is very short and extremely reliable.
2 Fingerprint sensor selection
In fingerprint products, fingerprint sensors and fingerprint algorithms are key. The process of fingerprint processing is to collect the fingerprint image and then process the fingerprint image. Therefore, whether the fingerprint image can be collected is the key to fingerprint processing. The fingerprint sensor is the collection component of the fingerprint image. Therefore, the performance of the fingerprint sensor will directly affect The performance of fingerprint products.
Currently used fingerprint sensors are mainly classified into semiconductor fingerprint sensors and optical fingerprint sensors. The semiconductor fingerprint sensor is further divided into a surface fingerprint sensor and a strip fingerprint sensor (ie, a sliding fingerprint sensor/scratch fingerprint sensor).
The selection of semiconductor fingerprint sensors mainly depends on the following indicators:
(1) Antistatic performance, generally required to be greater than 15kv, otherwise it is easy to be broken down.
(2) Resolution. Generally, at least 256dpi is required. Otherwise, it is not easy to distinguish fine fingerprints. For example, banks, hospitals, supermarkets, etc. should not be applied.
(3) Adaptability to dry and wet fingers (especially fingers coated with hand cream).
(4) Service life requirements. The service life of the sensor is generally required to be used up to 1 million times.
(5) Product consistency and adaptability. People's fingerprints in different regions have different characteristics, so high-adaptive fingerprint sensors should be used.
Because the fingerprint reader in this article is as small as possible in the design, the AuthenTec AES2510 scratch-type fingerprint sensor is selected. The reasons for its selection are as follows:
(1) It adopts the latest "The Power of Touch" technology, which is contact type and is not sensitive to dry and wet fingers.
(2) Easy to use and can provide fast fingerprint imaging with navigation function.
(3) Features of low power consumption and small CPU usage.
(4) Large shipments and low cost.
(5) The size is quite small, only 12mm & TImes; 5mm & TImes; 1.86mm.
Its appearance is shown in Figure 2:

Figure 2 AES2510 physical map
3 Fingerprint algorithm selection
Fingerprint recognition algorithm is the core of fingerprint recognition. Common fingerprint algorithms include: BIOKEY fingerprint recognition algorithm, Fingerpass fingerprint recognition algorithm, TOUCHSEC fingerprint recognition algorithm, OpenBio fingerprint recognition algorithm, FAA fingerprint recognition algorithm, etc. Many domestic companies have also independently developed many patented fingerprint recognition algorithms. There are also many sources of open algorithms on the web. In the early stage of design, the use of open source code of the algorithm will cause inconvenience in debugging. At the same time, the index of the algorithm is not sure whether it meets the demand. The fingerprint identification algorithm of large companies generally has higher price and negotiation difficulty. Therefore, the most reasonable method is to select The recognition algorithm provided by the fingerprint manufacturer is developed and verified. The algorithm provided by Autlentec is relatively mature and reliable. Due to the use of its fingerprint sensor, the fingerprint recognition algorithm charges relatively low. If the usage is large, it can even be given free of charge.
In our design, the fingerprint recognition algorithm provided by Authentec is used. Finally, the design results are verified to meet the requirements in the falsification rate, the rejection rate and the comparison time.
4 main CPU selection
The main focus of the selection of the main CPU is the operation speed and power consumption. Some manufacturers' products focus on low power consumption, and some focus on operation speed. A set of test data from several vendors is shown in Table 1, which shows the time required for different CPUs to operate the fingerprint matching algorithm.
Table 1 Running fingerprint matching algorithm time comparison table
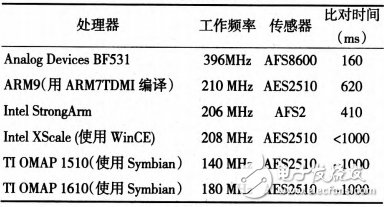
Because we adopt a hierarchical inclusive architecture, we don't care much about the power consumption of the main processor. Using a higher processing speed can give users a better experience. The CPU selected for this fingerprint lock is BF531. The ADSP-BF531 series processor is a member of the Blaclkflin series and is a highly integrated system-on-chip solution. Its functional block diagram is shown in Figure 3:
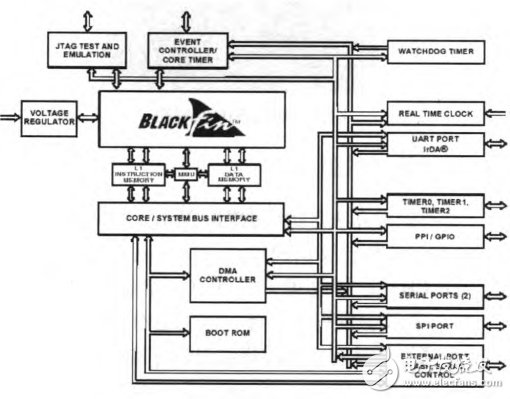
Figure 3 Functional block diagram of the BF531
The ADSP-BF53 l is a high-performance Black-fin processor with a frequency up to 400 MHz. Its core includes: 2 16-bit MAC, 2 40-bit ALU, 4 8-bit video ALU, and 1 40-bit shifter; For the fingerprint comparison calculation has a strong processing ability, in addition, the manufacturer also provides a fingerprint comparison algorithm tailored for the processor.
5 auxiliary CPU selection
Since the storage lock proposed by the fingerprint lock is 100 fingerprints, the required memory is more than lMByte, so an external storage device must be used. In order to minimize the cost, we use SDRAM chips to replace the external SRAM, so it will inevitably lead to an increase in the external power consumption of the device. For battery-powered devices, this is almost intolerable. For this reason, we use an ultra-low power. Auxiliary CPU is used for device management.
Normally, all the circuits of the main CPU are not powered. When the auxiliary CPU senses that there is a hand touch lock handle, the main CPU is powered on through the IO port. The main CPU and the fingerprint sensor start to work. After the fingerprint comparison is successful, the startup is started. unlock. Regardless of whether the comparison is successful or not, after waiting for a fixed period of time, the main CPU will enter an idle state, send an idle signal to the auxiliary CPU, and the auxiliary CPU powers off the main CPU.
Since the auxiliary CPU is long-term work and is always powered, the basic principle of the selection is ultra-low power consumption, simple structure and high reliability. This article selects TI's MSP430F2001. The MSP430 microcontroller has an ultra-low standby current of 0.5uA and a running power of 250uA/MIPs. It is an industry-recognized low-power microcontroller. It offers five low-power modes for battery-powered applications. The functional block diagram is shown in Figure 4:
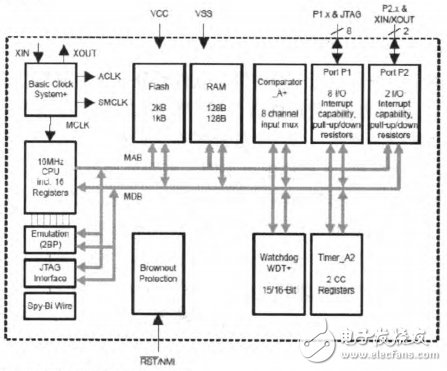
Figure 4 Functional block diagram of the MSP430F2001
The characteristics of the MSP430F200l are described as follows: low operating voltage (1.8V-3.6V); ultra-low power consumption (active mode is 220μA at 1 MHz, 2.2 V, standby mode is 0.5μA, off mode is 0.1μA); five power saving Mode; wakes up from standby mode for 1μs.
6 other
Other power reduction measures have been taken in this solution:
The LDO of the main processor is changed to a DC/DC switch chip to improve the power efficiency during operation;
The unlocking relay is first driven with a large current for 1 second to make it pull in, and then the duty ratio of the control terminal is adjusted to 30%, so that it is maintained for 4 seconds;
7 Conclusion
This design optimizes the circuit by reasonably selecting the device and surrounding the requirements of low cost, low power consumption, high computing performance, battery power supply, etc. The designed new fingerprint lock circuit has very large performance index, stability, low compatibility and low hardware cost. Advantage.
Through the design, several prototypes were produced. After only two No. 5 batteries were used, the locks were unlocked three times a day, and the work has been continuously and reliably for 2 years.
The fingerprint lock completed in this design can be widely used in many fields such as industrial door labeling, fingerprint attendance, and national defense security.
consumer transformer,audio isolation transformer,power low frequency transformer,epoxy encapsulated transformer
IHUA INDUSTRIES CO.,LTD. , https://www.ihua-coil.com