In the past 10 years, the number of electronic components used in automobiles has grown at an alarming rate. In-vehicle networks are also increasingly being designed or deployed in automobiles to connect multiple systems such as infotainment, car-assisted driving and security systems, often requiring a shared high-bandwidth infrastructure. At the same time, the in-vehicle network and the devices connected to it need to be diagnosed and maintained through an external interface. As car networking becomes more and more high, cars are actually becoming "networks on wheels," and security concerns about network infrastructure are increasing.
Although the possibility of an in-vehicle network being attacked is low, this does not mean that it will not happen. If there is enough time and resources, the hacker can launch a series of attacks, and it is possible to spread such attacks to all vehicles. In other words, a well-planned cyberattack will have a very broad impact. This is why car manufacturers and the industry itself are taking steps to ensure the safety of connected cars.
For the past 10 years, Ethernet has been the most popular and reliable network technology in the world, and has been successfully and safely deployed in a dynamic and ever-changing enterprise environment. Due to its high bandwidth, high cost performance, universality and inherent network security, Ethernet is increasingly used in automobiles. Ethernet's proven security has played a more significant advantage in automotive applications. In addition, since the equipment and configuration of the in-vehicle network are known and foreseeable, identifying and protecting them from threats is a very delicate process.
Basic principles of Ethernet
Message authentication and encryption are key features to ensure that car Ethernet is capable of preventing network damage. It provides the first invincible line of defense against malicious attacks. However, this feature alone is not enough to fully secure the connected car.
Ethernet uses a standard packet format that includes source and destination addresses, VLAN tagging, and frame verification, which provide the foundation for verification, isolation, and data integration. Furthermore, because the in-vehicle network design is precise and static, and has the characteristics of predictable traffic, it provides users with the opportunity to closely configure and constrain the network operation according to the design intent. For example, whether through static configuration or dynamic learning, Ethernet switches can use packet addresses for traffic isolation and filtering.
VLANs can be used to isolate different types of traffic on a shared physical network, ensuring that devices can only communicate with other devices in the domain. For example, a configured VLAN can be used for infotainment, while a single VLAN can be configured for car-assisted driving while the other can be used for security, and an Ethernet switch can enforce network isolation between the two.
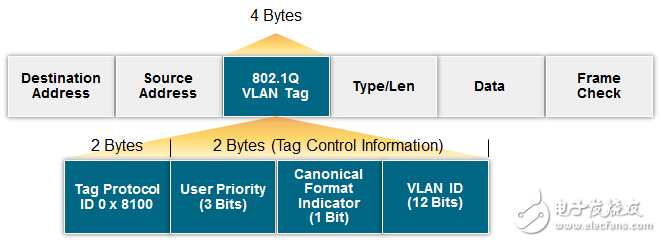
Figure 1: The Ethernet frame header contains the target MAC address and source MAC address as its first two fields, and a Cyclic Redundancy Check (CRC) for verifying packet integrity. In addition, it may include virtual local area network (VLAN) tags that define the systems and processes used by the bridge and switch to support VLANs.
An Access Control List (ACL) can be used to define a precisely configured action-following rule when a packet is forwarded, which defines which site can transmit traffic and where the traffic can go. When the specified traffic level is exceeded, Storm Control helps the switch monitor traffic levels and discard broadcast, multicast, and unknown unicast packets to protect the network from violating the offending site. At the same time, flow-based governance accurately defines and enforces bandwidth rules at each flow level, which protects the network from rogue software or error software. In addition, a wide range of data standards enable exception monitoring through software.
Device verification
Although each Ethernet packet contains the source MAC address, the MAC address may also be falsely reported. The widely implemented 802.1x standard is an option to verify device availability before entering the vehicle network. 802.1x defines a standardized method for transporting the Extensible Authentication Protocol (EAP) framework over wired or wireless LANs. This framework allows for the exchange and verification of security certificates before they are authorized to enter the network. EAP supports many authentication methods (such as EAP-PSK and EAP-TLS), each of which has its own set of authentication keys and certificates for device authentication. The strength of the verification varies depending on the method and certificate used, and can be pre-configured in a proprietary environment such as manufacturing or maintenance equipment.
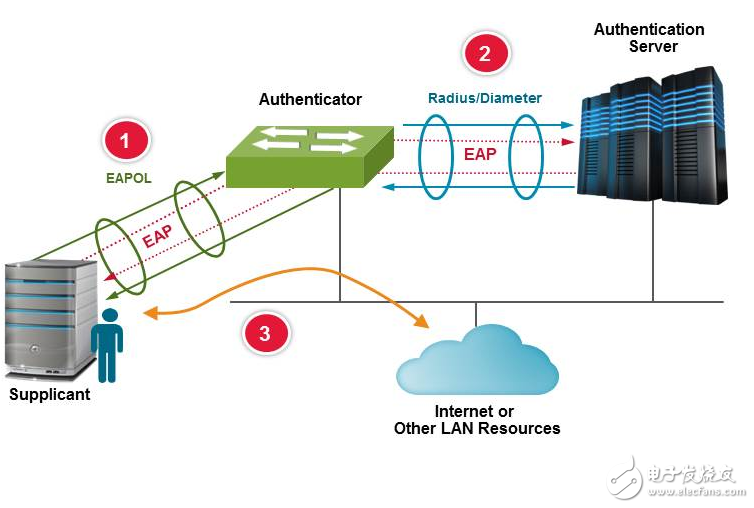
Figure 2: 802.1x defines a standardized method for transporting the Extensible Authentication Protocol (EAP) framework over wired or wireless LANs. This framework allows for the exchange and verification of security certificates before they are authorized to enter the network.
data encryption
Data encryption ensures that only authorized parties can access the encoded data. Many layers of the communication protocol stack, including the Ethernet layer, can be encrypted. The 802.11AE MAC Security Protocol (MACSec) standard uses the 802.1x standard for secure key exchange and provides MAC-level encryption and message authentication for Ethernet. However, because this method requires hardware support, which increases cost and power consumption, it is not supported by mainstream devices.

Figure 3: The inherent security features of automotive Ethernet may be the key to eliminating car safety hazards.
Although Ethernet has long been used as an IT network technology, it is undeniable that the application of this technology in the field of car networking is constantly being explored. Automotive Ethernet, the central backbone, provides automotive manufacturers with the tools they need to secure their network infrastructure. Even more gratifying is that Ethernet has begun to prove its worth.
This article is selected from the electronic enthusiast "Security Technology Special Issue", more quality content, download now

Aluminum circuit boards is a metal-based copper clad plate with good heat dissipation function. Generally, the single layer is composed of three-layer structure, which is a circuit layer (copper foil), an insulating layer and a metal base layer. Also used for high tech use is designed as double layers, the structure is circuit layer, insulation layer, aluminum base, insulation layer, circuit layer. A very small number of applications are multi-layer boards, which can be made of ordinary multi-layer boards combined with an insulating layer and an aluminum base.
Aluminum PCB characteristics
â— Surface Mount Technology (SMT);
â— Extremely efficient treatment of thermal diffusion in circuit design;
â— Reduce product operating temperature, increase product power density and reliability, and extend product life;
â— Reduce product size and reduce hardware and assembly costs;
â— Replace the fragile ceramic substrate for better mechanical durability.
Aluminum PCB use:
â— Audio equipment
Input, output amplifiers, balanced amplifiers, audio amplifiers, preamplifiers, power amplifiers, etc.
â— Power supply equipment
Switching regulator, DC/AC converter, SW regulator, etc.
â— Communication electronic equipment
High frequency amplifier, filtering appliance, reporting circuit, etc.
â— Office automation equipment
Motor drive, etc.
â— Automotive
Electronic regulator, ligniter, power controller, etc.
â— Computer
CPU board, floppy disk drive, power supply unit, etc.
â— Power module
Inverter, solid relay, rectifier bridge and so on.
â— LED lighting
With the promotion of energy-saving lamps, various energy-saving and beautiful LED lamps have been well received by the market, and aluminum PCB used for LED lamps have also begun to be applied on a large scale.
Aluminium Pcb,Aluminum Pcb Prototyping,Aluminium Pcb Board,Aluminium Circuit Boards
Chuangying Electronics Co.,Ltd , https://www.cwpcb.com