Discussion and Analysis on Security Technology of Digital Cellular Mobile Communication System
Keywords: digital cellular mobile communication system, security technology, authentication (authentication) and key distribution, encryption, intrusion detection system, 2G / 3G
1 Introduction
In mobile communications, if there are not enough security measures, users and service networks will face security threats such as wiretapping, impersonating users or networks, tampering with information, leaking confidential information, and denial of service. In terms of specific manifestations, attackers can use network protocols and system weaknesses to perform denial of service, location tracking, and intercept signaling and user data on the air interface, hijack calls or connections, and tamper, delete, and re-use sensitive data Wait for the attack. As a result, users cannot communicate normally and cause serious losses to users and service networks [1]. Therefore, secure communication has always been the focus of users' attention in mobile communication systems, especially in digital cellular mobile communication systems (hereinafter referred to as DCMCS).
Encryption technology is the core of realizing secure communication, and authentication (authentication) and key distribution are important guarantees for realizing secure communication. Intrusion detection is an important security monitoring technology. This article discusses and analyzes the three major security technologies in the DCMCS security system.
2 Security technology in 2G DCMCS
The security technology of 2G DCMCS is mainly based on authentication and key distribution (AKA) and wireless link data encryption. The 2G DCMCS currently in widespread operation is mainly based on the GSM system and North American DCMCS (DAMPS and N-CDMA, etc.). This section discusses and analyzes the AKA and encryption technologies of these two systems.
2.1 Authentication occasions in 2G DCMCS AKA
2G DCMCS generally supports authentication in the following situations: ①MS calling (excluding emergency calls); ②MS called; ③MS location registration; ④value-added service operations; ⑤switching. In addition, the North American DCMCS needs special authentication to update its SSD (Shared Secret Data) to ensure its security. In the GSM system, authentication is added when the CKSN (encryption key serial number) verification fails to ensure the safe implementation of encryption. CKSN verification itself can also be regarded as an alternative to authentication, that is, the process of "AKA → Encryption" is simplified as the process of "CKSN verification → Encryption", so as to avoid re-authentication every time encryption is performed.
2.2 2G DCMCS AKA algorithm and parameters
2.2.1 AKA algorithm and parameters of GSM system
The AKA algorithm in the GSM system is called A3 + A8 algorithm. It is managed by the MOU organization of GSM together with the A5 algorithm of data encryption. Both the GSM operator and the SIM card manufacturer must sign the corresponding confidentiality agreement with the MOU Get the specific algorithm.
Each user's SIM card stores a unique IMSI-Ki pair, and also saves the IMSI-Ki pair (encrypted by the A2 algorithm) in AuC. The A3 algorithm has two input parameters, one is the user's authentication key Ki, and the other is RAND (128 bits) generated by AuC. The operation result is an authentication response value SRES (32 bits). MS and AuC should use the same parameters and algorithms to get the same SRES, and the network should verify the user's identity accordingly. The operating entity of the network side A3 algorithm can be either MSC / VLR or HLR / AuC.
2.2.2 North American DCMCS AKA algorithm and parameters
The authentication algorithm, voice and signaling encryption algorithms of North American DCMCS are collectively referred to as the CAVE (cellular authentication and voice encryption) algorithm. CAVE is controlled by relevant US government regulations (ie, ITAR and Export Management Regulations) and only provides users with standard algorithms interface. There are two kinds of algorithms related to AKA in CAVE, namely authentication signature algorithm and SSD generation algorithm. An important difference from the GSM A3 algorithm is that: under different authentication occasions and authentication modes, the composition of the input parameters of the CAVE algorithm is different, and the effect of the output value output in different occasions in the authentication signaling procedure is also different Yes, MS and network entities must provide or use these parameters and results as required.
2.3 2G DCMCS AKA procedures and mechanisms
The authentication procedure defines a series of interaction processes between the MS and each network entity in order to implement and complete authentication. The GSM system and North American DCMCS have significant differences in the specific implementation of authentication in each authentication occasion. Here mainly introduces the main features and processing mechanisms of the two major systems in the authentication procedures.
2.3.1 GSM system authentication procedures
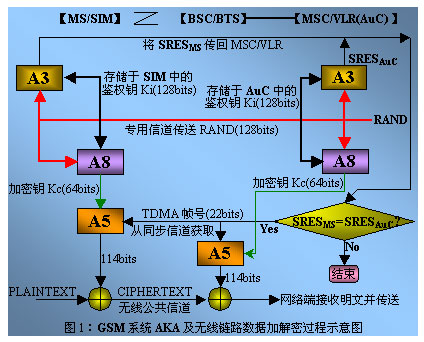
GSM uses the "request-response" method for authentication. Compared with North American DCCMS, the authentication procedure is much simpler. When authentication is required, the MSC / VLR sends an authentication command (including RAND) to the MS. The MS uses this RAND and its Ki to calculate the SRESMS, and transmits the SRESMS to the MSC / VLR through the authentication response message. Legal user, the authentication is successful. Otherwise, the authentication is unsuccessful, and the network can reject the user's business requirements. The upper part of Figure 1 is the AKA structure diagram of GSM. In addition, in order to improve the call connection speed, AuC can provide several authentication parameter sets (RAND, SRES, Kc) for each user in the network in advance, and the HLR will pass it to the response message when registering the MS location. VLR is saved for use. In this way, the execution time of the authentication program will not occupy the processing time of the user's real-time service, thereby increasing the call connection speed.
2.3.2 North American DCMCS authentication procedures
The authentication methods of the North American DCMCS vary according to different occasions, and the parameters involved in the authentication operation and the signaling process involved in the authentication will also be different.
2.3.2.1 Standard authentication method
This is an authentication method actively carried out by the MS. Standard authentication will be used in the following three occasions: â‘ MS calling; â‘¡MS called; â‘¢MS location registration. In this authentication method, all the MSs in the cell share the RAND broadcast on the forward channel / paging channel of the cell, and then the MS provides the calculated response value AUTHR and AUTHR through its initial access message during system access. Corresponding RANDC, and MS can also increase the internally saved COUNT count value by 1, and the result value is also placed in the initial access message to the network side. The initial access message may be location registration, call origination, etc. Therefore, this form of authentication has no explicit procedures on the A interface, and its message process is implicit in the corresponding initial access message.
In standard authentication, the network needs to perform three checks: RANDC, AUTHR, and COUNT. Only after these three checks are passed, the MS is allowed to access. â‘ RANDC test: it is to verify whether the random number used for MS authentication is generated by this switch; â‘¡AUTHR check: it is similar to SRES check in GSM; â‘¢COUNT check ("clone" detection): it is to identify There is an effective means of "clone" MS. If a MS is "clone", as long as both legitimate MS and "clone" MS are used online, the COUNT value provided by the two machines will definitely be different, due to network records The COUNT value is the sum of the number of call occurrences of the two machines, so any one of the two machines must have a different COUNT value from the COUNT value saved by the network when a system access attempt is made. It can be concluded that there is a "clone" MS. In addition to denying access, the network can also take measures such as tracking the MS.
2.3.2.2 Authentication method for unique features
This is an explicit authentication method initiated by the MSC to the MS. The message process is independent of the message process such as call origination, paging response, or registration. The MSC can instruct the base station to send a specific message to an MS on the control channel. RANDU for authentication. In the following occasions, the unique feature query authentication method will be used: ①handover; ② authentication on the voice channel; ③ possible re-authentication after standard authentication failure; ④ MS requests operations related to value-added services. ⑤ When the SSD is updated. The MSC can initiate the unique feature query procedure at any time. The most typical case is to implement this procedure at the beginning of call establishment or registration. Of course, this special unique feature query authentication process can also be added after a handover or standard authentication failure. MS calculates AUTHU with RANDU and sends it to MSC / VLR through a special authentication response message.
2.3.2.3 Authentication method for SSD update
It is a top-level security measure that is mainly used in situations: â‘ regular SSD updates; â‘¡ SSD updates that may be performed after standard authentication fails; â‘¢ other management needs. Since SSD is an important parameter to participate in the calculation under the first two authentication methods, SSD data needs to be updated frequently and the initiation of SSD update and confirmation of update results can only be completed by AuC, and cannot be performed in MSC / VLR. During the update process The SSD, MIN, ESN numbers cannot be transmitted in the air, so it must be accompanied by base station inquiry and unique authentication during the SSD update process. The intermediate response value AUTHBS during the base station inquiry process confirms that the MS and the network side SSD have been updated consistently .
It can be seen from this that the authentication mechanism of North American DCMCS is much more complicated than that of GSM system, which is mainly determined by its security and confidentiality system and its algorithm itself.
2.4 Wireless link data encryption in 2G DCMCS
In DCMCS, user information and important control signals can be encrypted when they are transmitted on the wireless channel. After the authentication is passed, the GSM system uses Kc = A8Ki (RAND) and A5 algorithm to encrypt user data and important signaling. North American DCMCS uses A-key and US public encryption algorithms to encrypt user data and important signaling. The lower part of Figure 1 is a schematic diagram of data encryption and decryption.
3 Intrusion detection technology in mobile communication network
Intrusion detection is an important security monitoring technology, the purpose of which is to identify the unauthorized use of intruders in the system and the abuse of legitimate users of the system, and try to find the system caused by software errors, the failure of the authentication module, and inappropriate system management Security deficiencies and take corresponding remedies. Intrusion detection system (Intrusion DetecTIon System: IDS) can be used to detect the misappropriation and misuse of network resources by illegal users and dishonest legal users in mobile communications. The security technologies such as AKA and encryption analyzed above can reduce the risk of attacking the mobile communication network by counterfeiting legitimate users and eavesdropping. However, for theft of mobile phones, security vulnerabilities in software and hardware platforms, use of network tools, and deceptive behaviors with the consent, it is not enough to use security technologies such as AKA. In order to improve the security of mobile communications, IDS can be used to monitor user behavior on the network side to reduce the threat of fraudulent attacks such as counterfeiting.
3.1 General IDS model
Figure 2 is a general IDS model that does not depend on special systems, application environments, system defects, and intrusion types. The basic idea is: the intruder's behavior and the abnormal behavior of the legal user can be distinguished from the normal behavior of the legal user. To define a user's normal behavior, a series of behavior profile configurations must be established and maintained for the user. These configurations describe the behavior characteristics of the user's normal use of the system. IDS can use these configurations to monitor current user activities and compare them with previous user activities. When the difference between a user ’s current activity and previous activities exceeds the threshold of each profile configuration, this current activity is considered abnormal And it is probably an intrusion.

3.2 Design of intrusion detection system in DCMCS
The early IDS was mainly designed for the security requirements of fixed networks, and the design of IDS in the mobile communication network must consider the user's mobility. The first IDS was designed for AMPS analog cellular systems. By designing the status of user activities in the IDS monitoring and reporting system for the mobile communication network, potential intrusion activities are detected in real time as much as possible. This can prevent dishonest legitimate users and illegal users from attacking the system.
3.2.1 Multi-level intrusion detection in DCMCS
Hierarchy (1): Verifies the user's moving speed and parallel, thereby performing rapid intrusion detection; Hierarchy (2): Module-level verification: The system detects whether user behavior conflicts on the DCMCS entity (such as a switch in a low-density user area There may be a symptom of intrusion when frequent handovers and calls occur; Level (3): Monitoring detection for each user: This is the most typical analysis of intrusion detection, which requires IDS to learn the normal behavior of users and create normal behavior of users The ability of profile configuration, under this premise, if an intruder requests network services, it will inevitably produce a deviation from the legal user's behavior profile configuration, so IDS can detect intruders based on the intruder's abnormal activities.
3.2.2 Design Ideas and Design Principles of 2G DCMCS IDS
3.2.2.1 Design Idea
Modify the existing HLR and VLR databases and add some intrusion detection routines. The user behavior monitored by IDS should include call data records and user location information. If the monitored data exceeds a certain threshold, corresponding alarm information and treatment measures will be given.
3.2.2.2 Design principles
Because IDS regards call data and location information as the main source of monitoring information. If all the audit data of mobile users is analyzed, then intrusion detection, the monitored user information should be transmitted to the processing part of IDS, which will endure a large communication delay. Therefore, when designing DCMCS IDS, you must pay attention to these design principles: â‘ Modify the existing mobile communication network system less; â‘¡ Design a fast algorithm so that it does not have prior knowledge of user behavior to track intruder ; â‘¢ In order to detect an intrusion activity, the communication volume between each unit of IDS should be as small as possible, so as not to cause a large additional overhead in the mobile communication network to reduce the communication performance of the system.
3.2.2.3 Design ideas for reference
Document [5] gives an effective IDAMN for designing IDS structure under DCMCS environment. Compared with existing IDS, IDAMN has many advantages. Please refer to this document for details.
3.2.3 Design points of 2G DCMCS IDS
3.2.3.1 Contour configuration
It can be seen from Fig. 2 that the core of IDS is the selection of thresholds for judgment conditions and the extraction of user's normal behavior features. In DCMCS, the user's profile configuration consists of three parts: â‘ mobility profile configuration; â‘¡ normal active profile configuration; â‘¢ user's voice profile configuration.
3.2.3.2 Establishment of contour configuration
The user's mobility profile configuration enables IDS to detect the user based on the user's movement in the network. This is mainly because the roaming of mobile users in the network is not completely random. Generally speaking, each user has a certain activity law. We can obtain the user's mobility profile configuration through a graph with the transition probability. Each vertex in the graph represents a location area, and the migration probability represents the frequency of mobile users moving in adjacent location intervals. The route formed by the edge with a large probability of migration is the location area where the user frequently appears, which also represents the activity law of the user. The calculation of the state transition probability can be obtained by statistically calculating the user's past activity, or a self-learning system can be designed using the idea of ​​neural network, and the mobile user's past activity is used as a training sample to learn it to extract the state transition probability . In this way, a user's mobility profile configuration can be obtained. The user profile information of normal activity profile configuration and voice profile configuration can be obtained from the user's past activity statistics.
3.2.3.3 Application of contour configuration
IDS will calculate each deviation of the user's activity behavior from its normal behavior profile configuration during detection. When the deviation exceeds a given threshold, an alarm message is issued, and then the alarm message is analyzed by a rule-based system and the final decision is given. If an intrusion activity is identified, IDS will notify the system to activate a corresponding intrusion processing routine to refuse service to the suspicious user or directly cut off the user's connection to the network.
3.3 Intrusion detection and AKA and confidentiality
Even if an intruder successfully circumvents the security mechanisms such as authentication and confidentiality of the system, because its purpose of intrusion is to make extensive use of network services, its behavior will inevitably be very different from the normal activity profile of the impersonated user Large deviations may be easily detected by IDS.
3.4 An Intrusion Detection Example Scheme for DCMCS
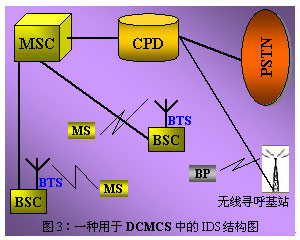
The scheme structure of this example is shown in Figure 3. Among them, CPD (Calling Profile Database) is the core of the entire IDS, which records the normal communication behavior characteristics of legal users in the system. MSC is responsible for real-time transmission of each user's communication behavior to CPD and centralized processing by it. When the CPD believes that there is an illegal intrusion, it sends a warning message to the wireless paging system, which sends the warning message to the pager carried by the impersonating user. CPD also accesses PSTN. Users can directly contact the CPD center through the phone to confirm whether their mobile phone has been stolen; at the same time, users can also modify their own CPD communication behavior description table at any time.

4 Comparison of security systems in 2G and 3G mobile communication systems
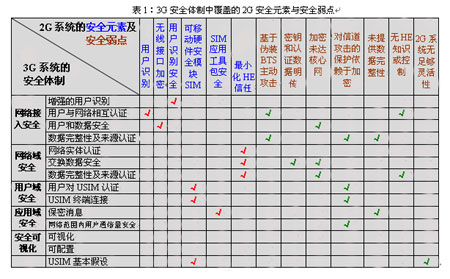
The security system of the 3rd GeneraTIon Mobile CommunicaTIon System (hereinafter referred to as 3G) is based on 2G, which retains and improves the security elements that have been proved to be necessary and robust in GSM and other 2G and improve Many security vulnerabilities in 2G [8]. By taking effective measures such as authentication, encryption, and integrity protection, 3G's security mechanism effectively guarantees the correct transmission and use of data. In addition, the security mechanism of 3G is also extensible, which can provide security protection for future new services. 3G will also provide users with security visibility operations, users can always check the security mode and security level they use. 3G will eventually provide new security features and services. Table 1 summarizes the 2G security elements and security weaknesses covered by the 3G security system.
5 Conclusion
Due to the openness of the air interface and the defect of the security of the communication protocol, the security problem of mobile communication is caused. Therefore, users have put forward higher and higher requirements for reliability and security in mobile communications. Security technologies such as encryption, authentication (authentication) and key distribution, and intrusion detection are particularly important. Although the safety technology in the existing DCMCS can meet the current user's safety communication needs. However, how to learn from each other's strengths, research and determine a more complete security technology system for the third and fourth generation mobile communication systems based on the existing technology should be the focus of the users and the industry.

Follow WeChat

Download Audiophile APP

Follow the audiophile class
related suggestion
The growing demand for data on global cellular networks forces operators to find ways to increase capacity by 5,000 times by 2030. To achieve this ...
The traditional cellular network consists of macrocells, and the coverage radius of each cell is mostly 1km to 25km. due to...
picoChip recently announced the launch of a complete eight-user WCDMA femtocell baseband (femtocell) baseband solution P ...
Rayspan Corporation announces the first LG chocolate handpiece of the first cellular phone with the company's metamaterial antenna ...
The integrated end-to-end architecture represents an important step towards commercial-grade LTE femtocell deployment. Ai ...
The official iOS 7 has a new feature that was not found in the beta version: cellular connection, Wi-Fi connection and Bluetooth connection can be simultaneously ...
Maxim Integrated will work with Freescale Semiconduc at the Mobile World Congress 2013 ...

At present, non-signaling technology is in the ascendant, mainly used to reduce manufacturing test time and cost, and is applicable to a wide range of technologies. Chipset manufacturers are ...
In the cellular mobile communication system, at the initial stage of network operation, the main goal of the operator is to build a large macro cell to obtain the greatest possible regional coverage ...
Ixia announced the application of new test standards, thereby redefining the evaluation indicators of operators' load distribution networks. Ixia's IxVeriW ...
What kind of shielding design method has the best efficiency? This three-part series of articles discusses effective RF screens around today's cellular transmission modules ...

People sometimes compare the multi-user of CDMA to the multiple piconets in DS-UWB, that is, the multiple access term corresponds to multiple overlapping in DS-UWB ...
1 Introduction Picocells are similar to home base stations (...
PicoChip launches complete system-level cellular solutions SoCs and software, picoXcell PC313 and PC32 ...

picoChip released its roadmap for LTE small cell system users in the next phase, and also established that the company is a family-based ...
Maxim's latest power management IC combines innovative adaptive charge pump architecture and advanced dimming technology to effectively extend battery life. S ...

What is Cellular technology Cellular Chinese meaning is "cellular (technology)", it is a kind of ...
What is a cellular system? Cellular means that the mobile network is shaped like cellular coal. The cellular communication system has experienced the first generation (1G) and the second generation (2 ...
The composition of the cellular mobile phone The cellular mobile phone system is mainly composed of mobile stations (car phones, mobile phones, etc.), wireless base stations and mobile phone switching centers ...
What is a cellular mobile phone? A cellular mobile phone refers to the division of a mobile phone service area into several adjacent cells, and each cell establishes a base ...

What is a cellular network? A cellular network divides the service distinction of mobile phones into sub-zones of regular hexagons, and each cell has a base station. form...
From the comparison between smart antennas and traditional cellular base station antennas, the possibility of TD-SCDMA group large network (macrocell) is the 12th work in the alliance industry group ...
Due to the decreasing deployment of cellular / 3G base stations, the sales of the RF power semiconductor device market for this field will continue to decline, making it difficult to change the recent ...
