After the Xu Yuyu incident, the discussion of topics related to telecom fraud continued to increase. At the Kcon conference held at the weekend, Only_guest, a PKAV hat with many years of research experience in telecommunications fraud, shared relevant issues. In addition to case studies, Lei Feng also selected several “cold knowledge†for telecommunication fraud for you.
1. Telecom fraud is much more profitable than operators Â
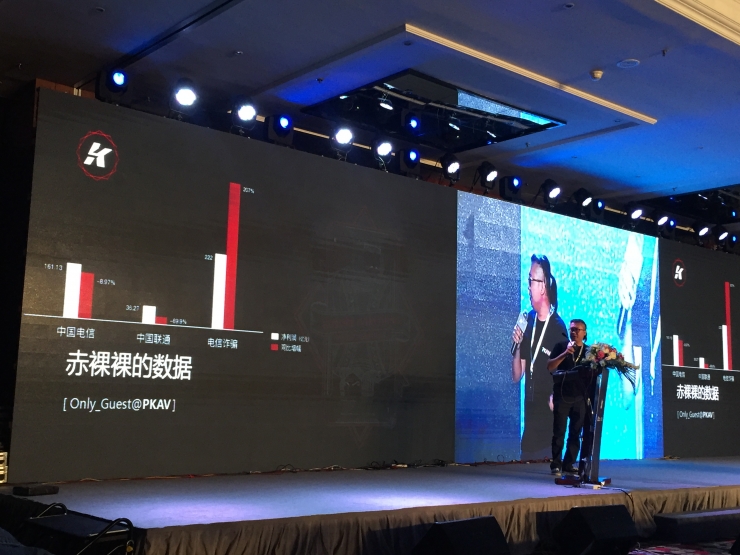
The data shown in the figure above is from the circle of friends of Only_guest. According to the introduction of Only_guest, two months ago, a friend of a bank commented on such a phrase in his circle of friends. The sum of net profit of China Telecom and China Unicom last year, and the total sum of profits of telecommunications fraud is not high. Subsequently, Only_guest found the data in the figure through the survey. The data shows:
Last year, China Telecom’s net profit was 16.113 billion yuan, a year-on-year increase of -8.97%
China Unicom's net profit last year was 3.527 billion, an increase of -69.9% year-on-year
The net profit of telecom fraud was 22.5 billion last year, an increase of 207% over the same period of last year
This group of naked data is extremely ironic, but it also exposes the temptation of huge interest in the telecom fraud industry.
2. Even if the caller number is 110, it may be a liar
O nly_guest introduced in the speech that there are basically two kinds of routines for telecom fraud, one is to send fraudulent messages via a pseudo base station, and the other is to make fraudulent calls via VoIP. Regardless of how clever scammers came up with swindles, the realization channels are basically these two.
The pseudo base station is a fake base station, which is generally composed of a host computer and a notebook computer. It is easy to carry and a backpack can hold all the equipment. Therefore, the liquidity is also very strong. A scammer carrying a backpack on a pseudo base station will be like a guerrilla warfare. He can change a place one day and one person can be a team. Â
VoIP is a network phone. VoIP technology is mainly used to digitize, compress, package, and encapsulate frames and other processes of traditional analog voice signals, enabling voice services to be carried over IP networks. VoIP services can be used not only between VoIP users, but also with phone users, such as users of traditional fixed-line networks and wireless mobile phone networks. Fraudsters use this technology to make arbitrary changes to the display number. Even if the caller number is 110, it may be a fraudster and it is difficult to trace it back.
Although relevant departments and operators have restricted pseudo base stations and display numbers that VoIP can change, and they are not allowed to be changed to the numbers of agencies such as the public prosecution department or banks, Only_guest told Lei Feng that the technical threshold for lifting such restrictions is not high.
3. Each scam undergoes "private customization"

Only_guest shared a common case during the presentation. Through the case, we can divide the entire fraud process into three parts.
The first step is to select the victim. Before swindling, the swindler will first perform information extraction and background images of the victim. It is usually preferred to start with people who have a certain social status and assets.
The second step is to customize the routine. According to the information of the chosen victim, the swindler will carefully tailor the cheating tool. Whether it is a page opened through a link or a phishing website, a filled-in form, and a downloaded control, it is based on real-world websites and controls that are copied or remodeled. Almost nothing can be detected by the victim.
The third step began to implement deception. The approximate process is as follows:
The liar calls the victim and tells the victim that the relevant department issued a warrant for you and freezes all your assets. Then he gives the victim a link. The link is a customized website page and the website of the relevant department looks Almost exactly the same, all information on the victim's page about the victim is accurate, and even the case number is true.
When the victim's trust is successfully defrauded, the victim will fill out an asset clearing form in the name of helping to unfreeze the assets, including the victim's bank information, online bank payment methods, and tools that need assistance. It is a dynamic password card. Or U shield and so on.
Fill out the form, the liar will let you download a similar to the online banking security controls and the like, click on the link, the fraudster will directly through the black screen connection directly to the victim's computer to control. (Black screen connection is usually not detected when the other party is connected to control your computer.)
When the fraudster uses the information on the form and computer to complete the transfer process, he will tell you on the phone that you can tell OK on the U shield or read the dynamic password to him. When this final step is completed, all the money in the victim's card is also transferred.
4. Before you defraud, transfer a dollar to the Red Cross
Only_guest told Lei Fengwang (searching for "Lei Feng Net" public number attention) that in their case of tracing investigations, it was found that in order to evade the pursuit and reduce the cost of defrauding as much as possible, fraudulent gangs usually have an overseas or Taiwanese IP and mainland IP. Overseas or Taiwanese IP transfers or money laundering, mainland IP distribution for specific fraudulent tasks, distribution of subordinates is using pseudo-base stations to send text messages or use VoIP calls to defraud staff.
While tracking, Only_guest also discovered that overseas or Taiwanese fraudsters with two different IP addresses may occasionally get together to “industry exchanges†or help each other with money laundering. Use jargon to communicate with each other, such as "washing carts" or "washing cars" is to wash big money or wash small money.
There is also a very interesting detail. Among the Taiwanese fraud scams they traced, a group of people were discovered. Whenever the victims were transferred, they would first transfer them to the Red Cross Foundation and then the victims. The remaining balance in the card is transferred to his own account. The specific reasons for this operation are unknown. Whether it is the transfer test operation or the desire to do good things, it feels ridiculous and ironic. Â
5. "Ghost" is the backbone of information leakage
For telecommunications fraud gangs, the first step is to obtain personal privacy information. In addition to underground black production, fraudulent gangs obtain personal information from the telecommunications operators, courier companies and even some government departments. On the 26th, there was a media explosion. An employee working at the Shunfeng Express Co., Ltd. in Hunan was accused of infringing on citizen's personal information and selling the company's system account number and password to others, resulting in the disclosure of a large amount of personal information.
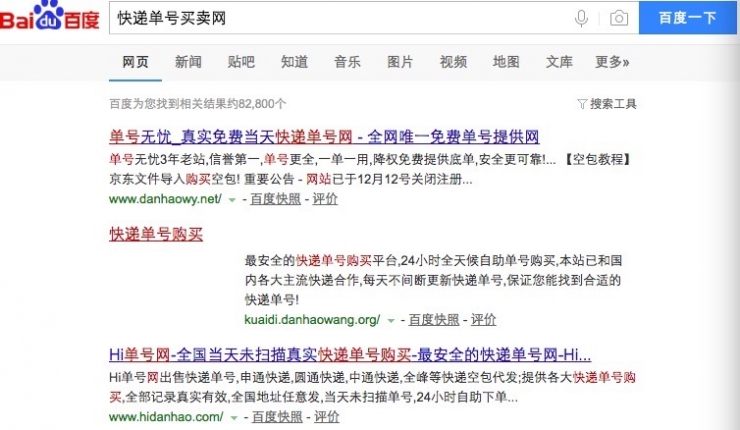
In fact, according to publicly disclosed judicial documents, incidents such as the sale of customer personal information by “Shun Feng Nei Ghost†are not uncommon. Through QQ search face group, you will find a number of groups that display information on the sale of face orders. In addition to SF Express, there are many other express delivery companies. A group named express delivery order purchase group announced on the announcement that each order is 3.5 yuan, a large quantity is favored, 50 single-buy, one-time purchase of 300, the price can also be preferential for 3 yuan. Through Baidu's search for sale orders, there will also be a lot of relevant information, and even there are purchases and sales transactions that can extract information on the list.
There are many unfamiliar “cold knowledge†about telecommunication fraud, and there are quite a few practitioners who are behind this industrial chain with great interests and temptations. The Xu Yuyu incident is not a single case. I hope that after the hot discussion, there will be fewer victims.
With Push-in connection technology, you can connect conductors easily – both directly and without tools, insert forces reduced by 50%. it is suitable for various applications. Insert rigid conductors or conductors with ferrules from 0.25mm² into the conductor shaft.The contact spring opens automatically and provides the required pressure force against the current bar.
When installing smaller conductors from 0.14mm², use a standard screwdriver to push the orange button and actuate the contact spring.
Push-in Connection have test and passed various certificates. For example, Vibration resistance in accordance with railway standard DINEN50155,shock and corrosion resistance in accordance with current shipbuilding registers.
Wire Terminal Block,Spring Terminal Block,Fixed Terminal Blocks,Push Terminal Block
Wonke Electric CO.,Ltd. , https://www.wkdq-electric.com