ARM Linux startup process is roughly: bootloader ---->kernel---->root filesystem. The bootloader gets control of the CPU on power-up, and the bootloader implements hardware initialization. The bootloader suddenly became the "first crab to eat" code after Power on.
When you talk about this, you have to think of how the hardware mechanism can satisfy this function. The CPU generally integrates small-capacity SRAM (also called stapping stone, stepping stone). When the system is powered on, the NAND controler automatically copies the front content of the Nand flash to the stepping stone. When the PC pointer is powered on, it points to the stepping stone. The starting address is 0x00000000. This part of the code can be implemented. So, this part of the code is the bootloader part. Can that bootloader not be able to get it running? This is indeed the case. In the embedded Linux software system, part of the nandflash code is usually the bootloader, then the kernel, and then the root file system.
Having said so much, it didn't seem to mention the start-up process. Don't worry, let's talk about it slowly.
To start the process, if you simply introduce where to go from and who is doing it, you may only know what you mean. Personally feel that with the CPU's PC pointer, follow the footprint of the code to clear the entire process, when the code is found in the implementation process, and then analyze the code, naturally know which part has completed what, more importantly, for The transplantation of code laid a solid foundation. This process of nature is painful and boring. Even after reading the code for a few days, it hasn't figured out yet, but it is also an exercise.
Bootloder
As mentioned earlier, the bootloader gets the cpu usage right on power-up, and of course it has to do some initialization work, such as turning off the watchdog, setting the operating mode of the cpu, setting the stack, and more urgent things. Of course, some other hardware of the motherboard must be simply initialized, such as the initialization of the external DDR memory, network card, display screen, nand flash, etc. Finally, it is also responsible for loading the Linux kernel into the memory. As the saying goes, responsibility and power are coexistent. You have rights, and of course you have to pay. When the bootloader finishes its mission, it will give cpu the right to use the next piece of code: kernel.
Kernel
Before discussing how the kernel starts, first understand the structure of the kernel and how it came about. The following figure shows the information displayed at the end of the kernel compilation:
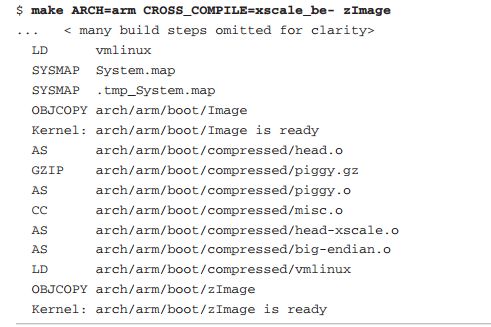
The following diagram illustrates the above compilation process.
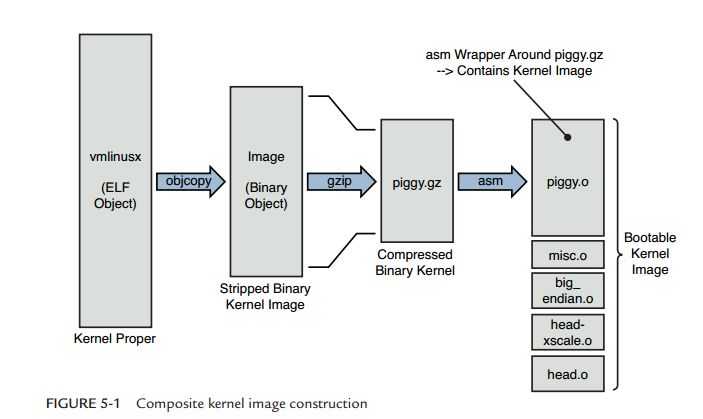
As you can see, several modules were compiled and linked after the kernel source files were compiled and linked into vmlinux files. Among them (1) vmlinux is the object file of ELF form, this kind of file is the file that each source code obtained after being connected, can't run on arm platform. (2) After the objcopy tool was converted, the binary format file Image was obtained. Compared to the vmlinux file, the image file was removed from many comments and debugging information. (3) After the image file is compressed, it gets piggy.gz. This file is just a compressed version of Image, and there is no other difference. (4) Then compile to generate several other module files misc.o, big_endian.o, head.o, head-xscale.o, these files form a component called bootstrap loader, also called bootstrap program. Compile the generated piggy.o file. (5) The last piggy.o file and the bootstrap loader form a bootable kernel Image file (bootable file).
You can see that the resulting executable file is the rightmost one in the above image. This is the image that we finally burned to the development board. Where piggy.o is the kernel image, and the remaining files constitute the boot program.
The following begins to discuss the CPU flow process, or use a diagram to show:
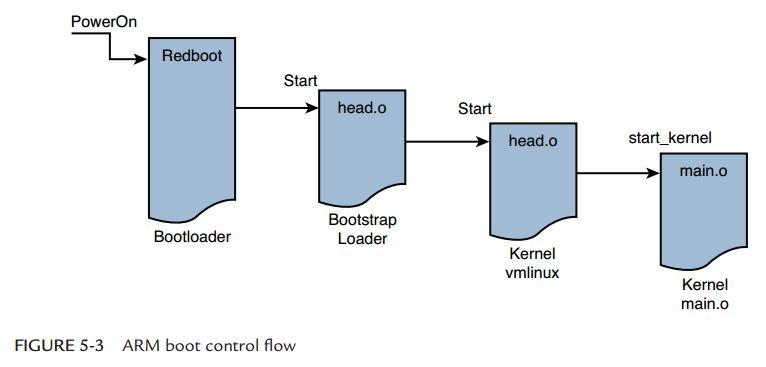
As can be seen from the above figure, the system starts executing the bootloader as soon as it is powered on. After the bootloader is executed, it passes control to the start label in the bootstrapper's head.o file. After the boot program finishes booting, it transfers control to the start label in the real kernel's head.o file. Department. Here is the entry point to the kernel. The head.o of the last kernel will give control to the start_kernel function of main.o. In this way, by looking at the corresponding code, you can know what the code is doing. Here we can find the appropriate code, analyze it, and see what they accomplish. Here is my analysis result:
Boot program:
Head.o takes control of the bootloader and completes the following tasks:
1. Enable I/D caches, close interrupts, create C runtime environment (ie set up stack) by head.o and head-xscal.o
2. Unzip and relocate the code, completed by misc.o
3 other hardware-related settings, such as big.endian.o big-end mode for the cpu
Kernel entry point: Take control from the boot program and complete the following tasks
1. Check for valid cpu and cpu information
Create an initialization page table entry
3. Enable MMU
4. Detect errors and report
5. Jump to the start_kernel() function in the kernel's own main.c file
Kernel startup:
From the kernel's head.o to take over the control, start the kernel boot, complete the initialization of the kernel, such as the initialization of the various subsystems of the kernel.
Root filesystem
At this point, the kernel completed the system hardware detection and hardware-driven initialization. The kernel space related work has been completed and began to transfer to the user space. The kernel space is excessive to the user space through an indirect initrd (a virtual file system), and then Begin to mount with the file system, the process: initrd ----> /sbin/init ----> /etc/inittab.
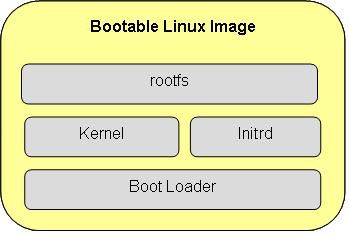
Initrd is a virtual file system with lib, bin, sbin, usr, proc, sys, var, dev, boot, and some other directories. Its directory is a bit like real, so we call it the virtual root file system. The role is to establish a relationship between the kernel and the real root file system, let the kernel go to the initrd to load the drivers needed by the root file system, and mount the root file system in a read-write manner, and let the first process execute the user. Init.
After init is executed, the /etc/inittab file in the system will be started to complete the system system initialization.
If you are tired of the original back of your phone, you should try our 3D Relief Back Sticker. The Back Skin Protective Film on the back can not only bring you a visual change, but also protect the back cover of the phone itself from scratches and collisions. Real 3D touch, personalized and stylish pattern design. Bring you a perfect experience.
In daily use, it can protect the equipment from scratches, dust, impact and other damage.
Long-lasting anti-scratch effect, significantly reducing dust, oil stains and fingerprint stains.
Easy to install, easy to stick to the back of the phone, and will not damage the original appearance of the phone.
With the Protective Film Cutting Machine, you can install the Back Film on different types of mobile phone back shells, including mobile phones, tablet computers and other electronic products. Customization can be completed in 30 seconds with just one click.
If you want to know more about 3D Relief Back Sticker, please click product details to view the parameters, models, pictures, prices and other information about 3D Relief Back Sticker.
Whether you are a group or an individual, we will try our best to provide you with accurate and comprehensive information about 3D Relief Back Sticker!
3D Phone Sticker, Carbon Fiber Back Sticker, 3D Relief Back Sticker, 3D Printing Back Sticker, Phone Skin,Mobile Phone Back Sticker
Shenzhen Jianjiantong Technology Co., Ltd. , https://www.hydrogelprotectivefilm.com