The morning news fan Fan reported on recent router security incidents. The routers adopting the Broadcom solution collectively recruited. There is a major security hole in the UPNP service that allows hackers to intrude and remotely control. This is an incredible task. Xiao Bian quickly gave everyone a temporary solution to make up for it.

The routers affected this time include D-Link/ASUS/NETGEAR/Linksys/Tengda and so on. Of course, this is not to say that all the routers of these brands are affected—only routers using the Broadcom solution will be relevant.
Tip: search for a specific router model, plus the keyword BCM, if the search results suggest xxx routing using BCM processor, it must be Broadcom's product, which is in the affected area.
There is a security hole in the UPNP service in these affected routers. This loophole allows hackers to remotely access your routes and can use the highest privilege ROOT. All Linux K26-based original firmware will be used!
The solution is to turn off the UPNP service, and before any new firmware can be updated, regardless of the brand, model, as long as the Broadcom program router, it is best to turn off this option.
Because each router's setting interface is different, Xiao Bian this only uses the ASUS routing firmware interface, other brands of routers need you to explore the specific UPNP settings page position.
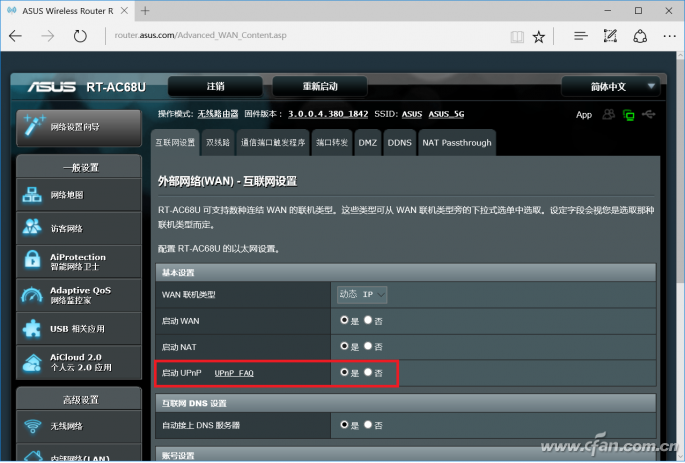
Tip: The full name of UPNP is Universal Plug and Play. The UPnP specification is based on the TCP/IP protocol and the new Internet protocol for the devices to communicate with each other. Simply speaking, the router will automatically map the required ports according to the application requirements of devices in the LAN (such as computers, tablets, and mobile phones), especially games and downloaded users. This function is simply an artifact.
However, when the UPNP service is closed, the router on the LAN will not be automatically assigned by the router when it requests the port. This requires the user to manually add it. At present, it is mainly the P2P download that requires port forwarding. This requires a specific analysis based on the specific conditions of the downloaded software. In addition, some routers have built-in port configurations for their own application software, such as the ASUS routers in the Xiaobian demo. Manually selecting applications and enabling port forwarding is fine, but there is no UPNP automatic intelligence.
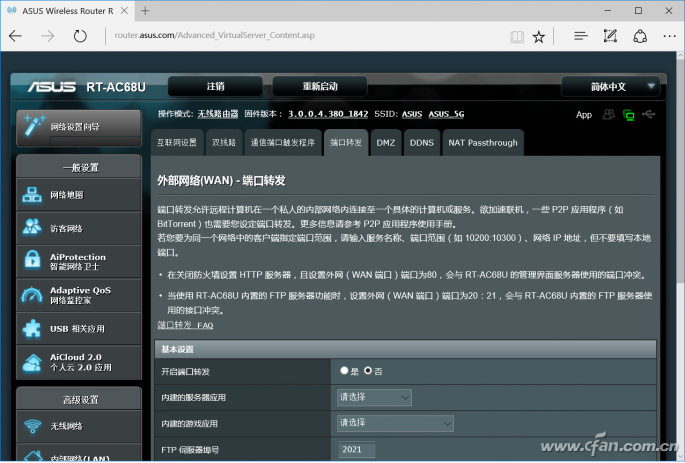
In addition, Xiao Bian also reminded everyone that it is best for the router to get the DMZ settings in the settings, and point the router's address to an IP address that will not be assigned in the LAN (such as 192.168.0.250, 10.0.0.254, etc. , as long as the LAN device does not use the IP can), so as to avoid external hacker attacks.
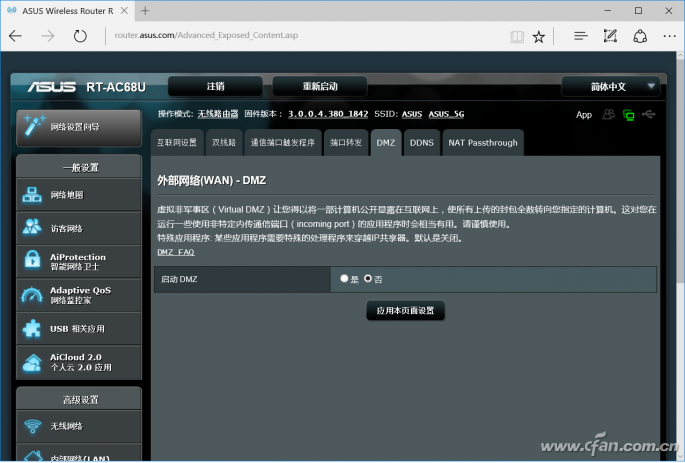
Of course, shutting down UPNP is only an expedient measure. After all, this feature is very useful. At this stage, we can only wait for each router vendor to provide an updated version of the BIOS, or explicitly inform users that this loophole has been fixed (but the geese have not yet done so. Out of response), hey, Xiao Bian distressed the user for a second...
Data Cable,Fast Data Cable,Data Power Cable,Data Transfer Cable
Guangzhou YISON Electron Technology Co., Limited , https://www.yisonearphone.com