The access controller is the hardware core of the access control system, and its quality and performance directly affect the stability of the entire access control system. As the core data processing and storage part of the access control system, the access control controller is responsible for setting the card reading permission and access permission of the entire access control system, monitoring the status of entrances and exits, recording access control events, and linking with other systems such as alarm and fire protection systems Important functions.
With the access control system playing an increasingly important role in the safety management of enterprises, the traditional mechanical door lock management has been unable to adapt to the safety management of modern enterprises, and its requirements are as follows:
Improving security: classify and assign time-based access rights management to designated areas, restrict related personnel from entering important areas at will, determine the level of access and allowable time periods for employees according to their positions and nature of work, and manage some important areas such as banks The vaults and subway control rooms are equipped with multiple entry and exit methods to meet better security requirements in the area and prevent internal and external theft.
Improve management efficiency: through the central management center to understand and set the status of each access point in real time, reducing the cost of personnel patrol. The system can record events in real time, which is convenient for enterprises to produce various personnel management reports such as attendance and scheduling.
Can be integrated with other systems: it can be integrated with fire protection, alarm and other systems to integrate a unified security platform to achieve accident warning and prevent various hazards. When a disaster enters a fire, the system can automatically open the door set in the control area, which is convenient for people to escape. Combined with the monitoring system, the access control system can automatically switch the photography screen, monitor and record the parts that need to be monitored.
Therefore, the stability and performance of the access control controller have also received more and more attention. The access controller must be able to establish communication with the computer, monitor the entrance and exit of each door in real time, and set up and analyze the card authority through the access control management software installed on the computer to query the access control entry and exit records and generate statistical attendance reports; once the communication is interrupted , The system can run normally offline. Therefore, a network access control controller that is safe, flexible, easy to expand, and can be integrated with other platforms will be the development trend of access control controllers.
The data transmission of the networked access control controller is more secure and stable, and can optimize the application of the existing resources of the enterprise.
The communication security of the access control system is the core of the access control controller. Most of the traditional access controllers use RS485 bus (half-duplex working mode), and then connect to the computer through RS485 to RS 232 communication. If you need to connect to the network, you need a network converter. In practical applications, there are poor real-time performance and easy data. Loss and other disadvantages. The IP-based networked access control controller has a built-in TCP / IP network interface, which can be directly built on the user's existing TCP / IP network. The high-speed communication rate can ensure that the device status is transmitted to the central server in real time, and the event record can be uploaded to the computer immediately And immediately displayed to prevent the loss and tampering of information. It is connected to peripheral devices such as card readers through the internal interface module of the controller. At the same time, it is convenient to install and can be expanded in time according to customer needs, saving costs.
The VertX network access controller specially developed for access control applications can be directly constructed on the user's existing TCP / IP network. Not only does it achieve anti-disassembly and anti-destruction in hardware protection, but also adopts multiple protection technologies in software. For example, RS485 communication at the scene uses encrypted communication to effectively prevent illegal eavesdropping, and at the same time AES encryption is used for TCP / IP network communication; the most important access control database in the system must be interpreted and read by special supporting software; the controller is built in Linux operation The system is not only stable in operation, but also safe and reliable. At the application layer, it not only provides basic anti-trailing, anti-foldback, anti-coercion and other security functions, but also can provide double-door interlocking and video surveillance linkage and other security extension functions.
The VertX system adopts a distributed network architecture with centralized management and decentralized control, which not only can ensure the centralized processing of information and control, but also can limit the scope of failure. Even if some equipment fails, it will not cause the normal operation of other parts of the entire system. When the system server is disconnected from the network, the VertX system can also automatically switch to local independent operation to keep the system running; and the VertX system has its own line inspection function, which automatically alarms when a faulty component is found, reduces the fault response time, and simultaneously passes the double 485 loop The design can ensure that when a fault occurs in the working loop, it will not affect the stability of the entire system.
(Picture 1: Normal state) (Picture 2: Somewhere disconnected)
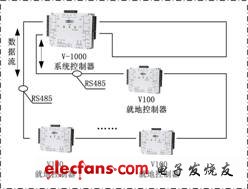
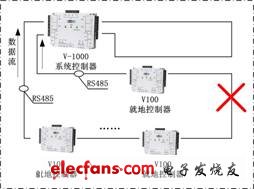
Take the two-level management and three-level control distributed network structure solution designed by HID Global for the Beijing Metro Fangshan Line as an example: the central management level can manage and view the access control functions of all stations in the system, which meets the company's flexibility to improve management The requirements of network and network failure. At the same time, the management level of each station can also independently manage and control the access control system within the jurisdiction; ensure that each station-level system does not depend on the external communication environment and service environment and can operate without the central server network, even if the subway communication backbone network occurs Failure, can effectively access the access control function in the jurisdiction, and after the communication is restored, upload all event information to the central management station to achieve real-time data transmission and effective monitoring.
The three-level control includes PC remote control, main station access controller (V1000) control, and local controller (V100) control. PC remote control can be used in some high-security places, and it is manually released after confirmation by the personnel of the management center; the main controller control is suitable for conventional access control; the local controller is suitable for the local controller can not communicate with the main controller At the time, emergency management of the access control equipment under management. Each station access control main controller V1000 manages the local level access control equipment V100 through the loop bus embedded in the line detection function, to ensure that the normal work of the access control system is not affected by a single point of failure, and at the same time, the line problem can be sent to the management workstation at the first time Send an alarm signal.
In addition, the HID VertX network controller is designed with a dual TCP / IP link to provide a reliable connection between the host controller and the network. When the current TCP / IP link is disconnected, the main controller can activate the backup connection to form a second TCP / IP link to ensure that each device can operate stably online. The HID VertX access control solution has three operating modes: online, offline and disaster. In addition to normal operation, it can record and transmit information in real time. When communication is interrupted, the controller can perform corresponding operations according to the authorization rules and store the corresponding information. Automatically upload and download related information to avoid the lack of information.
The controller with built-in network interface is very convenient for the deployment of access control system, especially for the application of more scattered buildings, which can save the user's comprehensive wiring cost. E.g. HID VertX V2000 controller utilizes the network facilities already laid in the early stage of Fuxi Power Plant to connect the host computer and other equipment on the TCP / IP network. Through software control of the access control system, it solves some departments including the network relay room and coal transportation complex. The area is far away and the difficulty of rewiring is required, which saves investment in construction and rewiring.

The networked access control system is more suitable for the integrated construction and security management of the overall security platform.
The networked access control controller adopts the industry standard TCP / IP protocol as a general protocol, which can be almost barrier-free in terms of system compatibility, so it can integrate the access control system into a unified security platform. At present, the more mature integration is the linkage with the monitoring system and the fire alarm. When the card swipe occurs, it will be linked with the camera in time to prevent illegal entry, or in the event of a fire, the fire control system can be used to control the access control system. In addition, through the software, the access control system is integrated with functions such as attendance, patrol, conference sign-in, and visitor management to achieve a wider range of applications.
The flexibility of the HID VertX controller comes from the system's modular design and open development platform, as well as good compatibility with peripheral devices. The hardware of the VertX controller adopts a modular design, with a network-controlled V1000 controller, a V100 interface module that connects the card reader and the door control device, a 16-zone alarm input module to monitor the status of peripheral devices, and 12 channels to control other devices The alarm output module, and the V2000 controller that combines network control and double door control, can be matched according to the user's on-site needs, forming systems of different sizes ranging from a single office to a global enterprise and offices around the world. And there is no capacity limit, and it can be expanded at any time in the future; all the interfaces of the peripheral devices use standard or universal interfaces to provide good compatibility, such as card readers (HID / non-HID) that support all Wiegand standards Universal low voltage 12V input and output, network communication uses common TCP / IP communication protocol, etc .; its open architecture allows users to freely match the system software, customize the required configuration and access control applications, customers can customize their own unique according to the needs of the scene Application software interface.
In order to make the living place safer, we need to build a strong security network to ensure the safety of the entire city. Under this premise, the modular design of the HID VertX network controller can be used to monitor and alarm in the construction of the urban security emergency system. , Fire control and other systems integration to realize the construction of a "safe city", transforming urban security from "post-event control" to "pre-event prevention", improving the safety of the city and the comfort of people's lives.
Bluetooth Speaker,Outdoor Bluetooth Speaker,Hifi Bluetooth Speaker,Round Bluetooth Speaker
Comcn Electronics Limited , https://www.comcnspeaker.com