Lei Feng: According to Wang Jun's pea pods, this week's tech circle was scraped. Although many of the small and fresh companies did not have any special feelings before, this time, the marriage with Alibaba was still eye-popping. The new generation “Internet Red†of the internet car, the Roewe RX5, was also released earlier this week.... For more exciting interpretations, please click the link below to read.
1, multi-faceted pea podsToday (July 5th) afternoon, pea pods officially announced that its application distribution business will be incorporated into the Alibaba Mobile Business Group, and both parties have officially signed a merger and acquisition agreement.
In China's Internet start-up companies, pea pods are an alternative, and the outside world is the easiest place to perceive its alternatives. It is its brand.
In fact, objectively speaking, the business of pea pods was put in the PC era more than ten years ago. In fact, it is similar to the role of Huajun Software Park.
The internal welfare of pea pods is one of the best I have ever seen in domestic startups, not one.
The major problems encountered in the company, the management will very frankly answer the staff's problems, after the completion of major projects, project managers will share with everyone, and answer the corresponding questions.
The pea pod engineer culture is very strong. Within the company, product designers and engineers are the project leaders; operations, markets, and business status are ranked second.
......
Pea pods are a company with a lot of IQs and can be troubled by emotional intelligence.
A voice of a person who once worked in a pea pod.
The author describes the author of this article division Beibei (WeChat public number: digital_meme), who once worked for pea pods, after entering LinkedIn, leaving LinkedIn to become the chief content officer of Zhengyang New Media.

Jeff Bezos founded Amazon in 1995. Twenty years later, Amazon’s market value has reached US$340 billion, making it the world’s largest online retailer and the second largest internet company in the world, second only to Alphabet (Google).
Since its listing in 1997, Amazon’s operating income has grown nearly exponentially, but in most cases it’s losing money. What does Bezos think? How is it persuading Wall Street and investors?
Regardless of how the competition chooses, Amazon uses its best strategy and never considers compromises: it also offers unlimited choices, top-tier shopper experiences, and lowest prices. For 20 years, this strategy has never changed.
In fact, it is very simple, Amazon will convert most of the costs associated with the shopping experience into fixed costs, such as unlimited choice of goods, personalized recommendations and so on. When the vast majority of shopper experience is a fixed cost, with the rapid growth of sales, the cost ratio of unit sales drops rapidly.
Bezos firmly believes that Amazon needs to define itself as a technology company, not a retailer.
Reading Bezos also learns that you can harvest what you want.
The author introduces the author of this article Liu Bin, Internet company strategic investment.

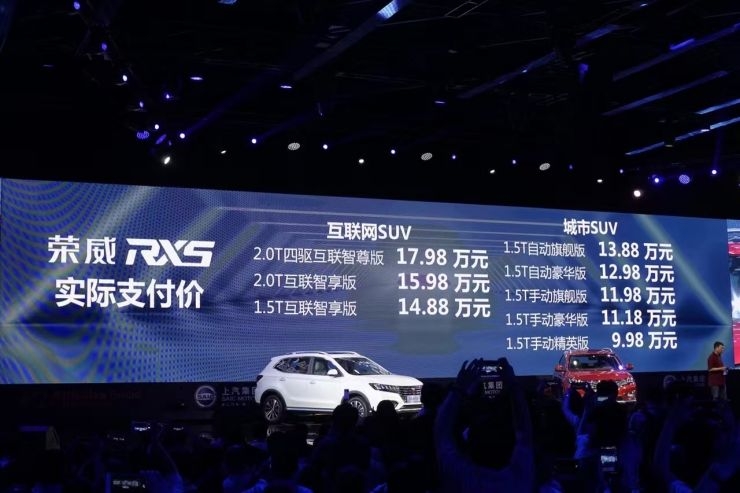
Today (July 6th), both the circle of friends and the media circle were smashed by the new generation of “net red†Roewe RX5. Chen Hong, the boss of SAIC Group, who has always been in suits and formal suits, even went into office wearing a T-shirt. Before Ma Yun came to power, the barrage of the live broadcast again exploded: "You are optimistic. My dad will be on the stage."
China's Internet is only 20 years old, but China is already the world's largest concentration camp for patients with Internet addiction... and the era of mobile Internet has completely "decentralized" the Internet to the extreme.
Perhaps contrary to many people's expectations, the history of car networking is much longer than that of mobile internet, and it can almost match the history of China's Internet.
1. RX5 is currently the most integrated product in the automotive and Internet field, and has paid a lot of labor and hard work.
2. Don't expect its Internet experience to reach 1/3 of your mobile phone.
What users want is the content and services of the mobile Internet. The automobile brand has the possibility of connecting the above content/service to the car. The actual content/service provider is the vertical field of each Internet.
Shen Rong Roewe RX5, see article.
The author introduces the author Li Linguo, an auto industry practitioner.
A key indicator of 5G is the transmission rate: According to the expectations of the communications industry, 5G should achieve transmission rates that are more than ten times faster than 4G, that is, 5G transmission rate can achieve 1Gb/s.
There are basically two methods to increase the transmission rate of wireless transmission. One is to increase the spectrum utilization, and the other is to increase the spectrum bandwidth. Compared to improving spectrum utilization, the method of increasing the spectrum bandwidth is simpler and more straightforward.
Now the commonly used frequency bands below 5GHz are already very crowded. Where can we find new spectrum resources? The method that most major manufacturers invariably think of is to use millimeter wave technology.
If you use the millimeter wave band, the spectrum bandwidth can easily be turned 10 times and the transmission rate can be greatly improved. In the 5G era, we can use the millimeter wave band to easily watch Blu-ray quality movies on the phone with 5G online, as long as you are not afraid of running out of traffic!
Millimeter wave technology how to bless the development of 5G, see article decomposition.
The author introduces the author of this article Li Yilei, UCLA doctoral student, Qualcomm (radio frequency group) student engineers, said (micro signal: silicon_talks) master pen.
The open letter mentioned that on March 8, 2016, the Beijing Public Security Bureau Chaoyang Branch criminally detained Yuan Wei on suspicion of illegally obtaining computer information system data; on April 12, the Chaoyang District People’s Procuratorate approved the alleged illegal acquisition of computers. Information system data crime arrest.
The crime of illegally acquiring computer information system data is a plot offense, that is, after a certain number of circumstances have been reached, it will be investigated for criminal responsibility.
Judging by the general public's acceptance or appearance of "permitting", perhaps Yuan Wei did not seek permission from Jiayuan Century, but at least before the Yuan Wei incident, Century Jiayuan did not communicate with Wuyun.com. Make explicit objections. Obviously, Yuan Wei is also a registered internship white hat of Wuyun. Its relationship with Century Jiayuan should be applicable to both previous behavioral practices.
After Jiayuan Network received information on the 42 previous loopholes, it could have made a written statement in the opposite direction and rejected the white hats of Wuyun.com again to detect its loopholes.
......
Finally, I ended up with a line of "Detective Di Renjie." Yuan Fang asks Di Renjie every time he has a suspicion. “The meaning of an adult is...†The great Diman standard replied “I don’t mean anythingâ€. Here, mystery, only the great talents of Di Dang know...
The author describes the author of this article Beijing Beijing (Shenzhen) Law Firm Liu Huabin.

The ATM attack is indeed the topic of the table in the 21st century. However, the history of the ATM itself can be traced back to the 1960s. This is almost the same as the term “hackingâ€.
In the early days, no one basically attacked it from the technical means. In essence, it was to remove the ATM from such a “tall†violent attack.
Today, there are several ideas for attacking ATMs:
One idea: Directly remove the ATM - start with the cash box.
Idea two: start from the network connection.
Three ideas: ATM Skimmer - start from the peripheral module.
The fourth idea is to implant a malicious program—starting from the computer part.
Four extensions of thinking: Using Windows XP features - still starting with the computer part
......
If you can prevent unauthorized media booting on an ATM, such as CDROM, U disk, etc., or modify the XFS standard as mentioned above, and encrypt the communication process, you can further effectively prevent problems from occurring.
The author introduces the original author Ouyang Ong, posted by FreeBuf's contributor Lei Fengnet (search "Lei Feng Net" public number attention) .

The driver’s death was caused by the automatic driving accident of Tesla this time. It has been nearly two months since the incident, but it has been a matter of several days in the media.
What may happen to an on-board computer that can be attacked, resulting in a serious accident?
Let's start with OBD II, the on-board diagnostic system in the United States. When the OBD II standard was established, there was no wireless interface on the car. Because of the signal connection of the wired network, an implicit trust architecture was constructed through the cable. Only trusted computers can connect to the network. The wireless network is a jungle. Everyone can eavesdrop, anyone can speak, and everyone can imitate others. To connect a device on a wired network to a wireless network is equivalent to throwing a group of embarrassing children directly into the food market. It is certain that a few are defrauded.
In terms of autonomous driving, the car has added new sensors and computers that traditional cars do not have. When the input data is disturbed, it may disturb the normal operation of the computer in the driving control network and cause an accident.
The third type of third-party program that causes the fault of the on-board system.
Learn more, click on the article to read.
The author introduces the author of this article: Song, co-founder and CTO of Seattle Newsky Security, a well-known antivirus expert in the industry, hacker.

Dongguan Pinji Electronic Technology Limited , https://www.iquaxusb4cable.com